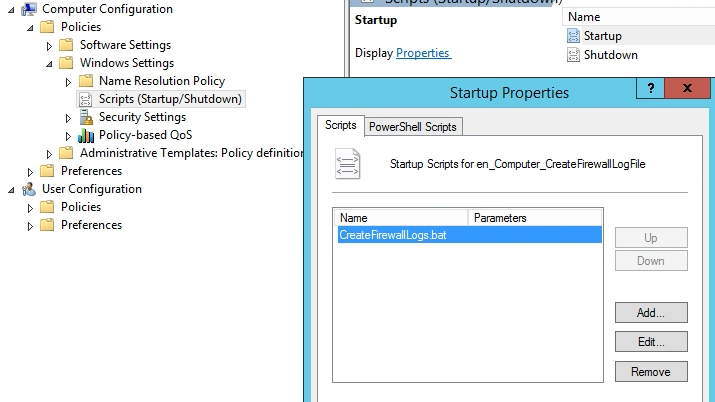
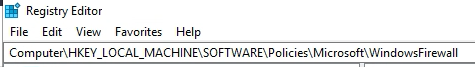
If you haven’t already forced ADFS to run on TLS 1.2 you are behind the curve. Activating TLS 1.2 on ADFS and turning off all other vulnerable services is relatively easy.
Step 1: Disable SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1, RC4 & Enable Strong Auth for .NET
The first step that always goes unsaid is to snapshot your Virtual Machines or get a solid backup state before making any changes to a running production environment. The next unsaid step is to perform these activities on a test/dev environment before taking down Production!
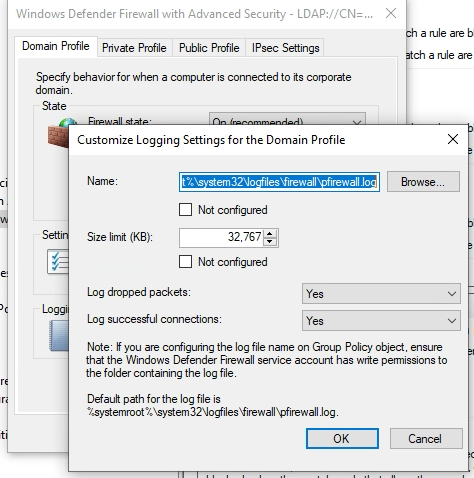
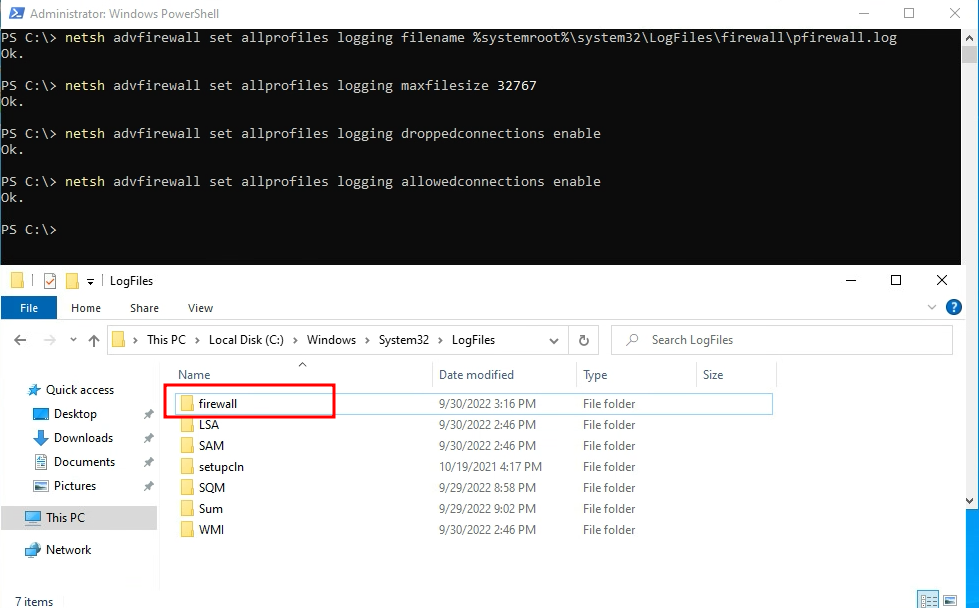
SSL 2.0 and SSL 3.0 should already be disabled, if they are not disable them immediately! The following link from Microsoft provides the registry keys and powershell needed to disable all of these services. Make sure these changes are being made on all Web Application Proxies (WAPs) and ADFS servers.
- Disable SSL 2.0
- Disable SSL 3.0
- Disable TLS 1.0
- Disable TLS 1.1
- Disable RC4
- Enable Strong Authentication for .NET Applications
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/manage-ssl-protocols-in-ad-fs
Step 2: Reboot all Virtual Machines / Servers
This step is pretty self explanatory.
Step 3: ADFS is Br0ken, Oh Noes!!
Disabling TLS 1.0 will break ADFS 3.0, more specifically it breaks the connection between the WAPs and the ADFS servers. This is easy to fix though.
Following this article on re-establishing the trust: https://blog.rmilne.ca/2021/11/16/ad-fs-web-application-proxy-re-establish-proxy-trust/
Quick Recap: Change this registry value on the primary Web Application Proxy:
HKLM\Software\Microsoft\ADFS\ProxyConfigurationStatus –> 1
This value normally has a value of 2 (which means configured), change it back to 1, and this change does not even require a reboot.
Open up Server Manager and launch “Remote Access Manager”, select “Web Application Proxy” and put in the required information to re-establish the trust.
You may need to reboot the WAPs one more time, I had to.
Step 4: Verify SSL Services are Correct
Once all services come back up, it would be a good time to verify that all the services you think you turned off are actually off. A SSL Server Test tool would be great for that, like the one by SSL Labs: https://www.ssllabs.com/ssltest/
Step 5: You may need to correct internal .NET Applications pointing to ADFS
Internal .NET Applications may start failing. If you start to receive error messages like “Authentication failed because the remote party has closed the transport stream”, it just means you are not specifying TLS 1.2.
There is a great article on Microsoft Docs here that explains the situation and the fix: https://docs.microsoft.com/en-us/answers/questions/400152/authentication-failed-because-the-remote-party-has.html
The developers will just need to specify the SecurityProtocol in their application.